As cyber attacks continue to mount and claim new victims, the cybersecurity industry continues to play catch-up, trying to fend off increasingly sophisticated groups of hackers. But it’s not working. With threats coming from all directions (cloud, mobile, social), network administrators are overwhelmed and under-prepared with their current toolset. It is obvious that new tools are necessary to battle these latest threats. Let’s take a look at the future of network security—biometric authentication in multi-layer security architecture.
Small but Pricey
Despite these hackers’ level of sophistication, many of the biggest attacks take advantage of simple security loopholes. Take Citigroup for example; their network was hacked after intruders were able to exploit a relatively simple vulnerability in their credit card customers’ website. Or the Government of Canada, whose networks were hacked when intruders were able to socially engineer passwords from unsuspecting employees. The problem is that networks that have a username-and-password system as their backbone are inherently insecure and susceptible to breaches.
A New Alternative
It’s time for a paradigm shift, one that adequately addresses the core problems affecting a network that is both practical and cost-effective in its implementation. While we believe that certain components are integral to the creation of a secure network, we do not think that there are any silver bullet solutions. With this in mind, we propose a system-architecture based on the following components:
Host-based Intrusion Detection System
A host-based intrusion detection system (HIDS) “monitors all or parts of the dynamic behavior and state of a computer system.” The HIDS software analyzes traffic coming to and from your machine, as well as all system files, in order to spot anomalies and threats. There are two types of host-based intrusion detection software: host wrappers/personal firewall and agent-based software; each has a different mechanism of detecting host-based intrusions.
Cisco and Symantec each have well-known versions of host-based intrusion detection software.
Network Intrusion Detection System
A network-based intrusion detection system (NIDS), in contrast to the host-based intrusion detection system, is designed to provide a bird’s eye view of the entire network, and in this capacity it allows detecting unwanted and malicious network traffic such as DDOS (denial of service attacks), scans, and other network-based attacks. The NIDS software analyzes all of the incoming packets to a network in order to try and detect suspicious patterns or anomalies; additionally, outgoing traffic and traffic generated inside the network is also monitored.
Well-known NIDS have been developed by Cisco, Q1 Labs; one popular signature-based NIDS is SNORT, which provides a free rule engine.
Continuous Authentication Solution
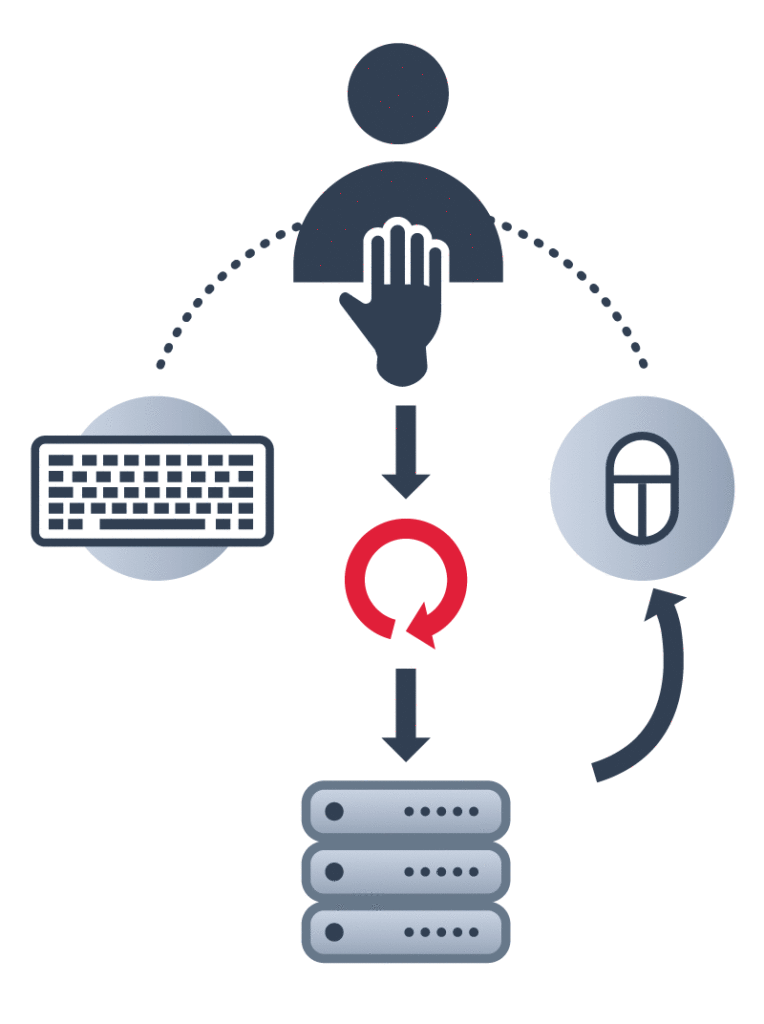
While NIDS and HIDS can help detect anomalies in traffic patterns and system behaviors, neither can identify anomalies in human behavior within the network. Behavioral biometric software can authenticate a user’s identity while they are logged into a network, between login and logout, based on certain behavioral patterns, which are analyzed in real time and continuously validated against a stored signature on the server. In this way, even if a hacker were to obtain the username and password of a legitimate user, they would be detected and logged out of the network.
Plurilock has developed Plurilock DEFEND, which is able to continuously authenticate users based on their mouse movements and keystroke patterns. Plurilock DEFEND secures the workplace without impacting business culture. Leveraging patented behavioral biometrics, the platform identifies people through their workplace behavior, maintaining an audit log, and autonomously challenging threats.
Virus Detector
With new threats from multiple directions coming every day, including the cloud, mobile devices, and social networks, top-notch anti-virus software is required.
Well-known anti-virus solutions are provided by McAfee and Symantec.
Firewall
Having a strong firewall to regulate incoming traffic remains an essential part of any network security architecture.
Forensic Analysis tools
In the event that an attack occurs, network administrators and forensic experts need to be able to access logs and event data to reconstruct the hack. Today, forensic analysis is a labor and data-intensive process that can take weeks to complete. Going forward software like Plurilock will make forensic analysis much easier.
Networks of the future will be much more secure when they are composed of multiple security applications that work symbiotically to identify and deter threats and hackers in real time. Multi-layer security systems will empower overburdened network administrators and give them the tools they need to keep valuable networks safe and secure. ■
















