There is always a sneaky temptation to avoid fiddling with production systems. The applications are up? The users are logging in okay and working? Then nothing needs to be done, right?
That sounds great until you become a statistic.
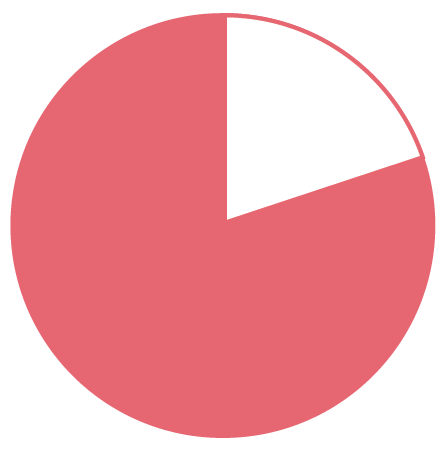
You know you’ve had that thought. Four out of five data breaches result from stolen credentials. That’s four out of five. Over 80 percent. Did you get that?
In fact, all the things that keep you up at night—zero-day exploits, SQL injections, buffer overruns, your provider’s security practices, and on and on—pale in importance when compared to one simple fact.
The Anonymity Problem
That fact? The vast majority of digital account credentials these days are effectively anonymous. Anyone who has them can use them to log in. Anyone. That goes for:
- User IDs and passwords, no matter how complex
- Secret questions, birth dates, maiden names, and other biographical data
- Hardware tokens
- Mobile phones and SMS numbers
If you think about it for a moment, that’s a startling list. It covers both the first authentication factor in use in a lot of places and the second. Maybe even the third.
One apparently obvious solution is traditional biometrics like fingerprints or face scans, until you realize that conference and expo attendees have in recent years seen:
- Fingerprint scanners fooled by rubber fingerprint copies
- Face scanners fooled by simple photographs

So yeah, maybe your biometrics infrastructure is great—if you even have it.
But have you tested it? If it’s like much of the biometrics infrastructure out there, it could ultimately be subject to the same anonymity problems as the other items above.
Plus Privacy Problems
As if that weren’t bad enough, many of the items above range from tricky to terrible from the privacy perspective.
When stolen, which ones may result in the release of sensitive, personally identifying information? Let’s see:
- User IDs
- Secret questions and biographical data
- Mobile phones
- Fingerprints
- Face scans
So—nearly all of them.
Fact is, today we’re widely relying on first- and second-factor authentication that is both subject to theft for illicit reuse and that results in serious loss of privacy when such theft occurs.
Not good.
Advanced Authentication (and When You Need It)
Plurilock’s™ advanced authentication technology is different. It relies for authentication on micro-patterns in movement (keystrokes, clicks, and similar inputs) along with patterns in environmental and contextual conditions.
This brings some key benefits.
It involves no biographical or body geometry data at all. So no privacy issue. It’s impossible to fool, since it relies on AI-analyzed patterns in real-time, moment-by-moment data. And it’s completely non-anonymous. Only one real person can authenticate for a given identity—the right person, with the right body. And no particular hardware is required.
When or why might you need advanced authentication like this? How about for:

-
Easy multi-factor authentication (MFA). You can finally deploy MFA without the extra hardware, costs, or user training that’s been delaying you.
-
Solving the privacy and privacy liability problem. Let’s say you’re breached. Let’s face it, it happens to the biggest and best—not to mention SMBs, over two-thirds of which experienced cyberattacks during 2018. If the worst happens, would you rather lose (a) raw numeric data that can’t be reused, or (b) personally identifying information that could ruin lives? (The answer is ‘a’.)
-
Lowering support and security costs. Security support eats resources. Users struggle with apps (and compatibility). They can’t receive their codes. Their secret questions don’t work. They lose their YubiKey or RSA token and you have to FedEx another one. They need a two-hour training session just to log in. Unless you use advanced authentication, that is. Advanced authentication is invisible and automatic.
-
Eliminating device requirements. A bank teller does not want to face a five-minute, hardware-involved login process. Neither does a doctor. Or a day trader. Or really anyone, for that matter. Advanced authentication enables MFA that adds zero time and zero extra steps to login. In the right cases, that’s a massive win.
-
Authenticating lots and lots of users. Sending out an RSA token or supporting one mobile authenticator app is a pain. Doing it for hundreds of users? Thousands of users? Tens of thousands of users? That’s not a pain, that’s a fully-staffed department. Advanced authentication eliminates the per-user overhead—it’s fingerprint-strong MFA on a password management budget.
-
Healthcare MFA. Or education MFA. Or finance MFA. In healthcare, there’s HIPAA. In education, there’s FERPA. In finance, PCI compliance matters. Whether you’re after healthcare MFA, education MFA, finance MFA, or MFA in some other industry, advanced authentication enables strong security for mere mortals (and their tired support staff).
-
Regulatory compliance in general. Best practices for authentication are clear these days, and there’s consensus about them. Combine shared secrets with additional identity factors. Ensure that they’re out of band. Don’t harm privacy in the process. Every standard and regulatory regime agrees on these items. Yet they’re hard to achieve—unless you use advanced MFA.
The Future is Better
The present is full of an unprecedented number of major data breaches—but thankfully, the future is coming. In fact, it’s here.

Plurilock isn’t the only company engineering this new breed of authentication technologies, but we’re sure we’re the best at it—with multiple patents and founders of the field in house (along with their decades of behavioral-biometric research). It’s used in our ADAPT, AWARE, and DEFEND products.
Whether you’re in healthcare or education and grappling with HIPAA or FERPA, in critical infrastructure or government services trying to protect state secrets or comply with ISO 27001, or just an SMB that needs to get MFA out stat—but can’t really cope with a bunch of new hardware requirements and privacy liability—you need to look beyond legacy MFA technologies.
Standards-compliant, regulatory-compliant MFA that can’t be fooled is here. It needs no hardware or training. It imposes no delays or extra steps. Real companies are offering it now—and it’s exactly what you need. ■
















