
ICS and OT Systems are Becoming More Frequent Cyber Attack Targets
The term “cyber attack” brings ransomware and stolen data to mind, but today there’s a quieter yet equally devastating war being waged against industrial control systems (ICS) and operational technology

ICS and OT Systems are Becoming More Frequent Cyber Attack Targets
The term “cyber attack” brings ransomware and stolen data to mind, but today there’s a quieter yet equally devastating war being waged against industrial control systems (ICS) and operational technology

ICS and OT Systems are Becoming More Frequent Cyber Attack Targets
The term “cyber attack” brings ransomware and stolen data to mind, but today there’s a quieter yet equally devastating war being waged against industrial control systems (ICS) and operational technology
Previous

Identity-Focused Attacks Are a Trend—Here’s How They Work and What To Do About Them
In today’s digital landscape, a single set of valid employee credentials can be all an attacker needs to infiltrate an

Cybersecurity Awareness Month 2024 Provides Four Simple Steps to Secure Our World
In today’s technology-driven world, Cybersecurity Awareness Month serves as an important reminder of the proactive steps we can all take

Uncovering Hidden Threats: The Crucial Role of Penetration Testing in Cybersecurity
In the digital age, where data breaches and cyberattacks are increasingly common, safeguarding your organization’s digital assets isn’t just an

Plurilock Critical Services Mobilizes Rapidly—and This Transforms Outcomes
Cyber threats are evolving faster than ever. From sophisticated ransomware attacks to state-sponsored espionage, the speed at which an organization

How Many Vendors Are Represented In Your Environments?
Our Critical Services team routinely encounters environments populated by multiple products from multiple vendors and multiple VARs or suppliers. In
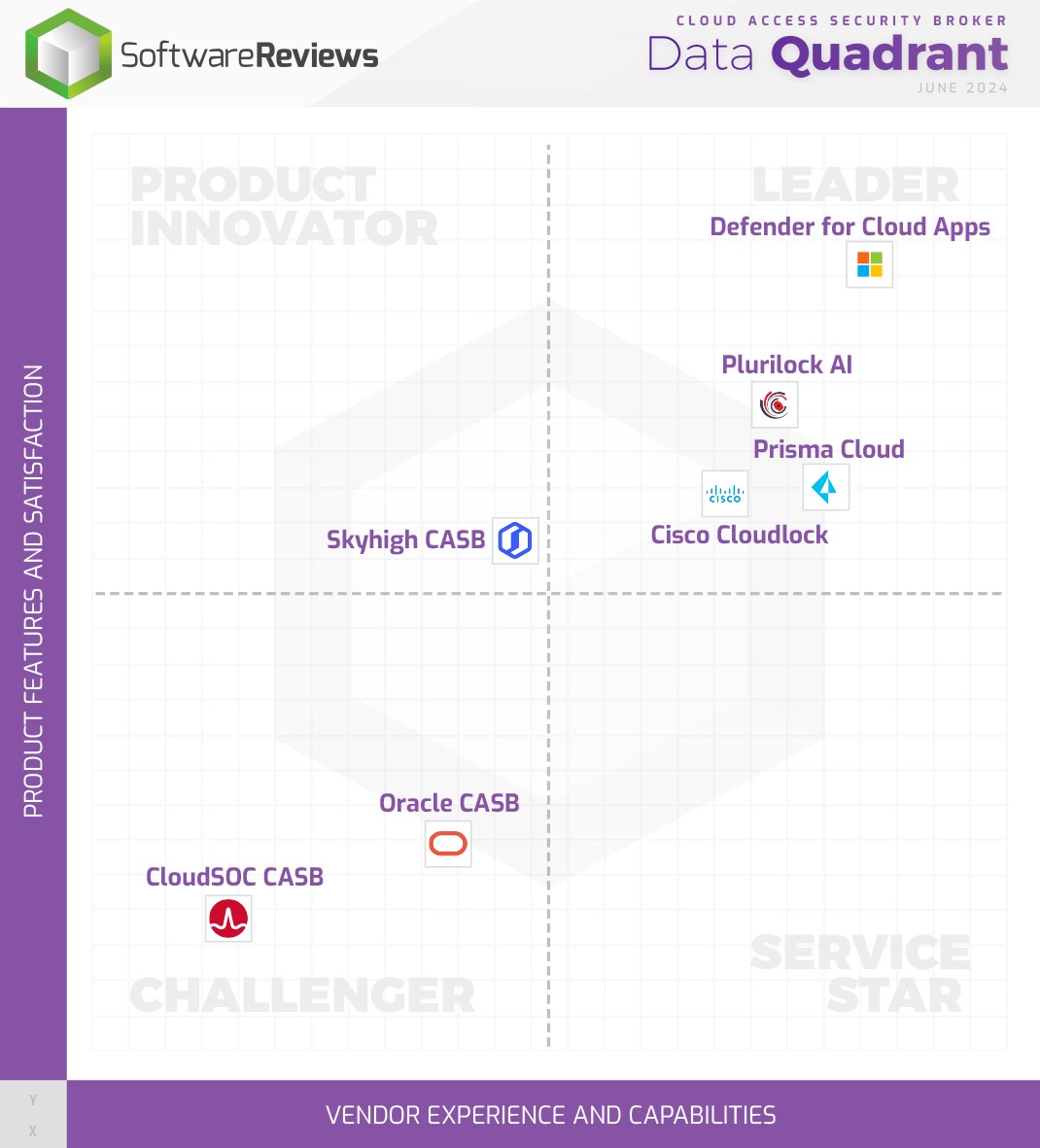
Plurilock AI is a Quadrant Gold Medalist for the Fifth Year Running
Don’t look now, but Plurilock AI has been named a quadrant gold medalist for the fifth year running by Info-Tech

Plurilock Critical Services Delivers the Capabilities You Need in a World of Increasing Risk
Data and security breaches. Regional warfare. Natural disasters. Pandemics and social crises. Supply chain instability and opacity. These are challenging

Pairing World-class Services with a World-class VAR Gives Plurilock—and You—Key Advantages
At Plurilock we’re both a consultant and services provider (through our Plurilock Critical Services unit) and a large technology reseller

How GDPR, CCPA, HIPAA, and Other Data Privacy Standards Safeguard Our Digital Lives
In the digital age, our lives are more connected than ever. We shop online, communicate through social media, store personal

Fortifying Education: A Guide to Cybersecurity Resources for K-12 Schools
In the rapidly evolving landscape of digital education, the role of cybersecurity in K-12 schools cannot be overstated. As educational

Bridging the Gap: The Challenge of Finding Cybersecurity Allies in the Midst of Crisis
In an era dominated by technological advancements, our dependence on digital infrastructure has never been more pronounced. However, with this

No, Cybersecurity Isn’t Beyond the Reach of Small Businesses and Organizations
If you’re a small business, a small organization of any kind, or an organization that lives at something of a

A Call for Responsible Governance of AI Use
In the dynamic realm of artificial intelligence (AI), organizations find themselves at a pivotal juncture, tasked with finding a way

Learning Technology in K-12 Schools Poses Unique Cybersecurity Challenges
Learning technology in K-12 schools poses unique cybersecurity challenges that aren’t often considered by the broader cybersecurity industry. Chrome OS

The Unparalleled Security Dance: YubiKey and Plurilock AI Cloud
At Plurilock, we understand the paramount importance of cloud security, and our mission since the beginning has been to pioneer

Empowering Insurance: The Role of Generative AI and AI Guardrails
In recent years, the insurance industry has undergone a transformative journey, leveraging cutting-edge technologies to enhance efficiency, accuracy, and customer

Lithium and Cobalt Supplies Are Among the Cybersecurity Battlegrounds Emerging due to Electrification
“Electrification” is one way to describe the fact that more things in the real world than ever before are now

How Digital Fatigue Turns Employees into Cyber Risks
In an era dominated by digital communication and information overload, the modern workplace is grappling with a silent adversary—digital fatigue.


IT and Cyber Services and Solutions
Zero trust, data protection, IAM, PKI, penetration testing and offensive security, emergency support, and incident management services.







