Full-day, real-time identity
without extra hardware.
Plurilock DEFEND™ Continuous Zero Trust Authentication
The Problem
Who's really using that session?
The world spends a lot of time locking down logins. Yet resources are scarce when it comes to rapidly detecting and monitoring compromised credentials and sessions.
Password policies, OTP MFA, company-wide SSO—all of it makes authentication and credentials harder to use without ultimately revealing the presence of illicit activity on stolen credentials.
The result? Intercepted sessions. Access with stolen devices. Unauthorized subcontracting. Insider threats.
Isn't there a better way?
See Plurilock in action
the solution
Plurilock DEFEND™ detects compromised sessions and credentials in real time.

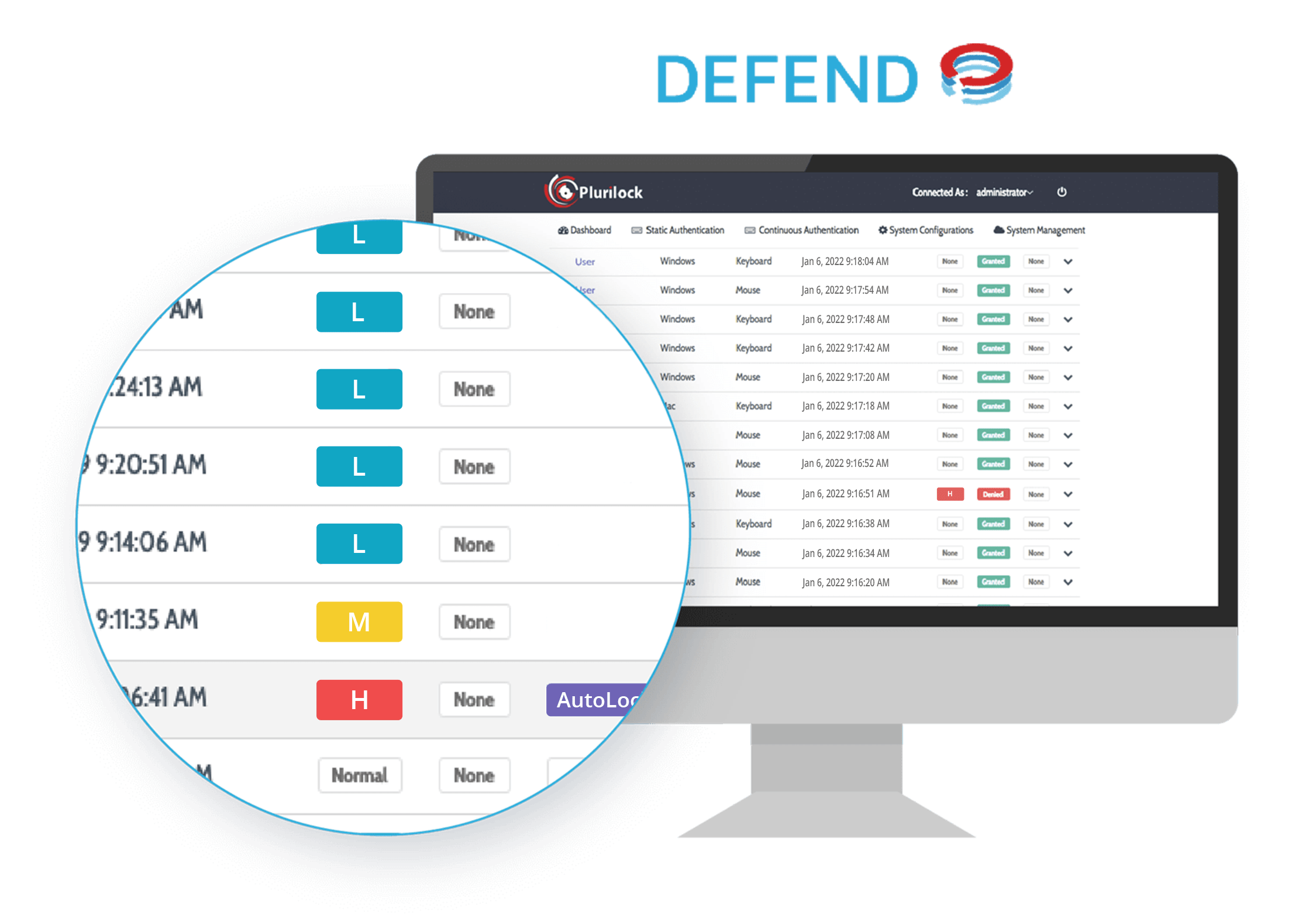
Know who's computing not just at login time but whenever work is happening on an open session, morning, midday, or afternoon.

Confirm a user's identity continuously, every 3-5 seconds, for the duration of open session work—no gaps or uncertainty.
Preserve a full-day identity trail with the standard keyboards and pointing devices already deployed—no devices to buy.

Know not just which account is responsible for key actions and events, but which human being is responsible, regardless of the account used.

Correlate well-defined periods of credential-to-user mismatch with interactive activity, child processes, and other key events and insights.
Add total identity awareness invisibly, without new tools, workflows, steps, or other hindrances to everyday work activity.
IDENTITY ASSURANCE IN VIRTUAL ENVIRONMENTS
Continuous zero trust identity confirmation
in Amazon WorkSpaces virtual environments
Plurilock DEFEND, now with advanced functionality in VDI environments.
- Provides continuous identity assurance for Windows devices in virtual environments throughout the session
- Protects BYOD and remote workforces, consistently throughout the workday, from credential compromise and unauthorized access
- Plays an important role in a zero trust architecture
Watch Video Representation
FIRMWare-embedded technology
Continuous authentication with self-healing capabilities from Absolute Software™.
Plurilock DEFEND, now with self-healing capabilities built in.
- Protects from attacks when malicious users gain administrative privileges
- Offers firmware-embedded architecture for self-healing capabilities
- Provides better protection than other OS-level application protection
How it Works
Award-winning, patented behavioral biometrics. Invisible identity verification.
Plurilock DEFEND relies on patented behavioral biometrics and machine learning technology to recognize users simply by the way they work—never what they are working on.

When user mouse movement and keystroke cadence matches their usual behavior, logs reflect little or no risk.

As keyboard and pointer movements begin to seem unusual for the user, medium risk events are logged.

When a configurable risk threshold is crossed, DEFEND notifies security staff and logs illicit activity.

Keyboard and pointer motion is analyzed as work occurs. When movements don't match a worker's usual patterns, DEFEND takes action.
Why It's Different
True continuous detection.
Many “continuous” solutions detect anomalies only at predefined times or in connection with predefined events. Others merely detect the presence or absence of a device, not an unknown user.
Plurilock DEFEND detects credential compromise continuously, all day long. It validates the presence or absence of a user—not just a thing.
Why It's enterprise-ready
Scalable and privacy-friendly.
The Plurilock DEFEND engine runs on a cloud server designed for fault tolerance and high availability to ensure nonstop identity verification.
Even better, Plurilock DEFEND compares credentials to actual user identity by analyzing simple keyboard and pointer motion—not link clicks, text entry, or other activity data—so it's privacy safe, too.
Where It Works
Broad compatibility. Environment-level deployment.


Plurilock DEFEND
Real-time credential and session compromise detection.
No added hardware.
Compare biometric identity to in-use credentials every 3-5 seconds, all day long. Detect compromises rapidly with the hardware you already have.

+1 (888) 282-0696 (USA West)
+1 (908) 231-7777 (USA East)
+1 (866) 657-7620 (Canada)
Advanced cybersecurity and Zero Trust
Security assessments and consulting
IT products and solutions
Professional services
Managed services






