Plurilock™ Tearsheets
Learn more about Plurilock products and services.
Plurilock Services Tearsheets
Expert-backed vulnerability assessments with prioritized tracking, testing, and remediation guidance for enterprise security teams.
Comprehensive evaluation of AI governance posture with structured recommendations for safe, strategic AI growth.
Managed data protection service combining DLP and insider threat capabilities as a service.
Advanced data protection architectures and engineering to safeguard your data against evolving threats.
Cross-functional rapid response teams providing immediate expertise for urgent IT and cybersecurity threats.
Continuous, adaptive identity and access management that protects against internal and external threats.
Always-on, proactive security approach that identifies, tests, tracks and mitigates dangerous vulnerabilities before exploitation.
Advanced PKI modernization and cryptography consulting services for enterprise security transformation.
Purple team collaboration with real-time feedback to simulate post-compromise attacker behavior across hybrid environments.
Advanced social engineering attack simulation including deepfakes, MFA bypass, and privilege escalation testing.
Comprehensive zero trust program evaluation with structured recommendations across all critical security domains.
Guidance and Recommendations
Sample, shareable addition for employee handbook or company policy library to provide governance for employee AI use.
Generative AI is exploding, but workplace governance is lagging. Use this whitepaper to help implement guardrails.
Cheat sheet for basics to stay secure, their ideal deployment order, and steps to take in case of a breach.
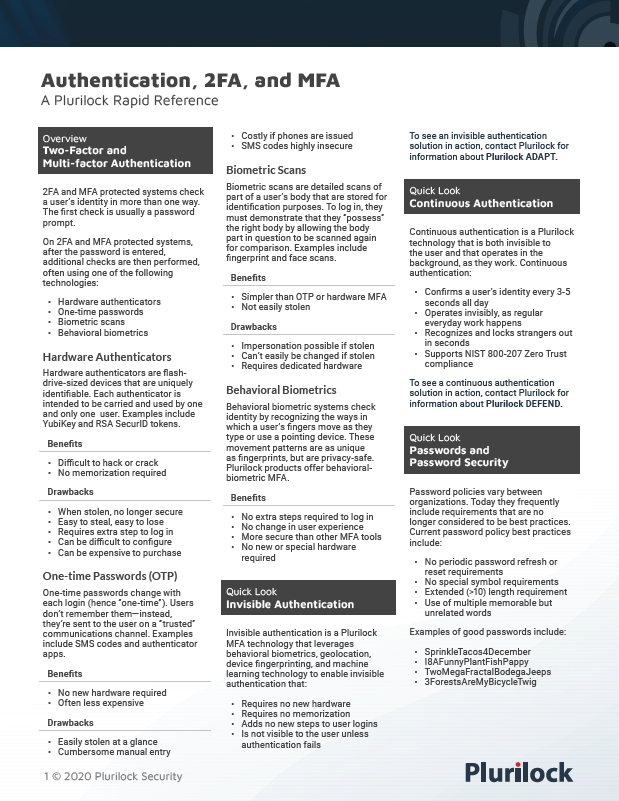
Concise rapid reference to 2FA, MFA, password best practices, and authentication vocabulary.
Plurilock AI Product Information
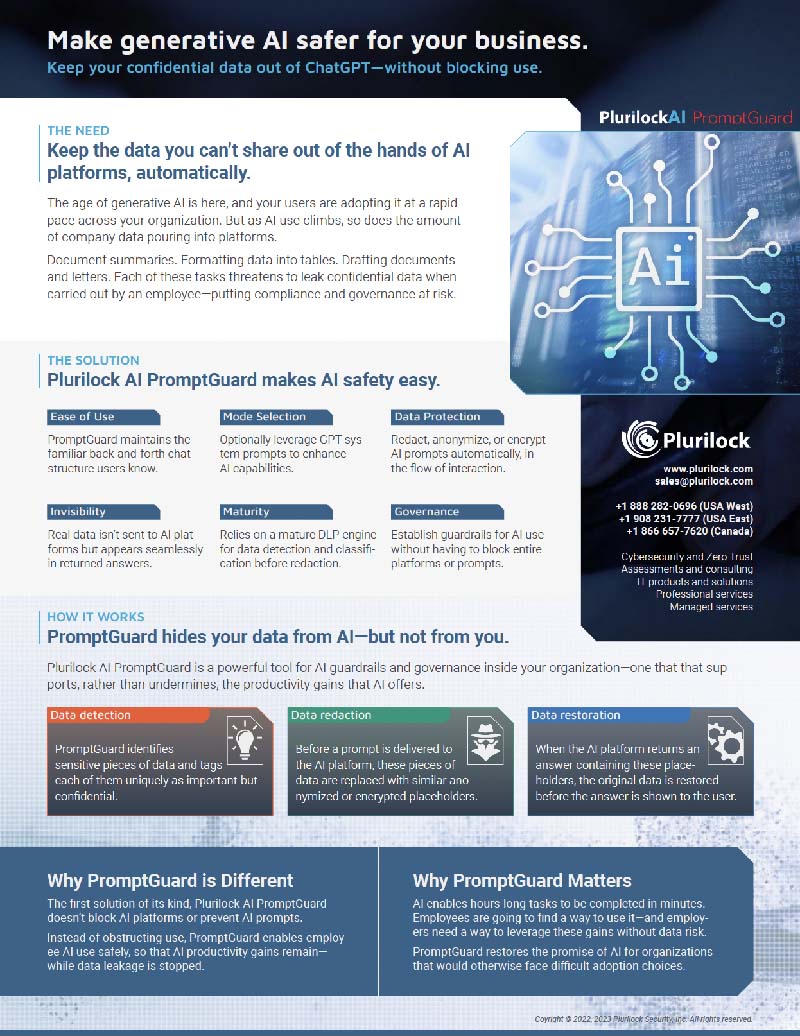
PromptGuard detects and hides confidential data from AI—but not from the user—to provide guardrails for AI use.